The IEC 62443 series of standards describes both technical and action-oriented aspects of industrial cybersecurity and is subdivided into different parts. It consists of a general part, guidelines and procedures, as well as system and component requirements. Certification in accordance with this series of standards is based on the following parts: IEC 62443–4–2 for products and IEC 61443–3–3 for systems. The first part of this series of standards, i.e. IEC 62443–4–1, focuses on process requirements for a secure development lifecycle. Depending on the individual certifying body, evidence of a secure development lifecycle can be a prerequisite for certification.
Security level for the system
The Capability Security Level (SL-C) is assessed within the scope of product or component certification. Thus, the Security Level (SL) actually achieved in a plant environment must be assessed separately, and relevant evidence must be provided. IEC 62443–3–3 defines system requirements for IT security. In terms of industrial automation technology, this part of the IEC series of standard is aimed at operators, system integrators, product and system manufacturers, as well as service providers. Furthermore, it serves as a basis for capability assessment in order to determine whether the Target Security Level (SL-T) required by the operator can actually be achieved.
There are seven foundational requirements :
- Identification and authentication control
- Use control
- System integrity
- Data confidentiality
- Restricted data flow
- Timely response to events
- Resource availability
These requirements rest upon security requirements (SRs – System Requirements) and enhanced requirements (REs – Requirement Enhancements). In addition, the requirements set out in IEC 62443–4–2 for software applications, embedded devices, host devices, and network devices apply to the component level.
The result is the Achieved Security Level (SL-A). Certification in accordance with IEC 62443–3–3 can refer to either the complete automation and control system or a subsystem. If a system or subsystem has been certified in accordance with this IEC standard, evidence of security capability is considered to have been provided for this system/subsystem. The explanations and information included in associated manufacturer reports and documents must be adhered to.
IEC-certified process control system
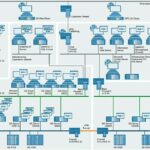
The Simatic PCS 7 process control system has been certified in accordance with IEC 62443–4–1 and IEC 62443–3–3. This means that evidence of capability has been provided for the components if the system structure complies with the reference architecture. Siemens provides comprehensive documentation for the SIMATIC PCS 7 control system. Compendium Part F includes information on Industrial Security. However, the certification of the components, or if the system itself, gives no indication as to the Security Level (SL) achieved by the plant.
The plant manufacturer must assess and verify the Security Level (SL) of each individual plant within the scope of plant creation. To this end, the plant manufacturer must provide evidence that the SL required has been achieved. Evidence can be provided by means of an assessment.
Cyber security in plant planning
IEC 62443 defines the strategies and procedures required for creating a plant in compliance with relevant security requirements. As an integral part of plant planning, the security concept should be set up at the beginning of the planning phase. This concept must be based on a security risk analysis, the result of which illustrates the minimization of risks. This analysis serves to determine the Target Security Level (SL-T) required for the individual plant sections and segments.
Afterwards, the measures necessary to achieve the Target Security Level (SL-T) required are determined on this basis – such as organizational measures, the limitation of intervention and access options, plant segmentation, malware handling, as well as updates. The concept and the measures must be consistently implemented; they provide the basis for the planning and selection of products, systems and network architecture.
Integrating security considerations from the very outset
Any retrospective analysis and subsequent implementation of the security concept involve huge effort and high costs. Necessary conversions might impact the network architecture or require the replacement of components. Therefore, it is advisable to implement and consistently apply a security concept right from the very outset. In fact, this is the only way to deploy suitable components. Component/system certifications can make it easier for the planner to identify the best choice. A final assessment of system security requirements is still required.
The Defense in Depth concept is a multi-layer model for ensuring security. Since several obstacles must be overcome, this concept makes it harder for an attacker to intrude on the system and cause damage. The Defense in Depth concept focuses on the plant, the network, and system integrity. Appropriate measures must be defined for all areas, assessed at regular intervals, and adapted if required. Especially for the chemical industry, the Namur Worksheet NA 163 “Security Risk Assessment of SIS” and the corresponding check list illustrate the procedure for this assessment.
A secure development cycle in compliance with IEC 62443–4–1 provides the basis for a secure product or system.
In general, the Security Level (SL) achieved by the plant must be finally assessed in order to provide evidence of compliance with the Target Security Level (SL-T) required.
Permanent cyber security
To keep a plant permanently safe, it must be subjected to regular maintenance. To this end, the information provided by the manufacturers must be observed and patches must be installed. Furthermore, a new security risk analysis must be performed at regular intervals and the measures must be adapted depending on the results achieved. Considering the fact that attack scenarios change continuously, this is essential and an integral part of the plant lifecycle. This is the only way to keep a plant secure. Organizations such as Namur publish guidelines that help to correctly apply the IEC 62443 series of standards.
Siemens AG, Nürnberg