The risk of becoming a victim of cybercriminals is higher in Germany than ever before. That‘s according to the October 2022 situation report by the German Federal Office for Information Security. So the question today is no longer whether you will be attacked, but rather: when. How can companies protect themselves effectively? And what is particularly important?
IT vs. OT Security Architectures
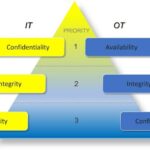
Traditionally, the Information Technology (IT) and Operational Technology (OT) ecosystems have been built in separate silos. For IT, confidentiality comes first, followed by integrity and availability (C-I-A), while for OT, availability followed by integrity and confidentiality (A-I-C) is at the top.
One of the key pillars of digital transformation is IT/OT convergence. Typically, IT and OT business units have been in separate worlds. The main reason for this was the need to protect physical operations from external tampering, but organizational and technological constraints also played a role. The IT/OT gap provides security for mission-critical systems, but also severely limits business efficiency, agility and access to information.
IT/OT convergence
Industry 4.0 technologies such as the Internet of Things (IoT), smart sensors and edge computing have already paved the way for convergence. IT/OT convergence advances the digital enterprise by empowering people and their workforce at all levels through digitization and automation.
To bridge the IT/OT gap, the first step is to break down the technology silos that IT and OT systems form. One of the reasons for the IT/OT gap is also the generally low level of cross-skills between IT and OT staff. IT and OT teams have different methodologies and cultures – and often conflicting priorities. Several options are available for integrating the IT-OT management triangle. The best solutions offer tailored approaches to enable IT, OT and management to work as one.
Security and organizational readiness also play an important role. As IT and OT converge, open architectures and a multitude of interconnected devices greatly expand the risk landscape. Another challenge is the integration of complex technologies and processes across the enterprise.
Holistic approach
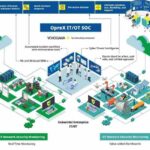
When neither IT nor OT security teams alone have the expertise to handle all of these processes, it becomes very difficult not only to collaborate, but also to protect against damage to the company‘s assets. This is where the security operations center (SOC) comes into play: Yokogawa developed an internal security monitoring service for Yokogawa Group IT infrastructure around the world in 2019. This service monitors PCs, DNS/AD servers, intrusion detection systems (IDS), and production systems 24/7, and uses cyber threat intelligence (CTI) and machine learning (ML) to process up to 600 million events per day. Now, Yokogawa has leveraged its OT security solution to develop an innovative cloud-based IT/OT SOC service. This service provides users with an integrated, consistent and holistic solution for maximum security in the IT and OT areas.
The central control center is responsible not only for all security-relevant services of IT, but also for those of operational technology as a specialized IT/OT SOC. Networked sensors, machines, systems and devices are monitored 24/7, security logs and anomalies are analyzed and protective measures are initiated to ward off potential attacks. Security experts from different areas work together with coordinated processes and special tools – people, process, technology.
People: Security experts are the most important component of a SOC. They are highly specialized professionals, each responsible for a specific area: technicians, analysts, pentesters, digital forensic experts, ethical hackers, etc.
Processes: The focus is on detecting, analyzing and responding to as yet unknown attack methods. Processes are defined on the basis of so-called „security playbooks“ and work is done with threat intelligence feeds as well as malware information security platforms in 24/7 service.
Technology: As a technical SOC foundation, a SIEM (Security Information and Event Management) uses various log files to identify incidents and provide early information on potential threats. Other tools include threat intelligence, vulnerability assessment, anomaly detection and incident handling & response.
By bundling competencies, SOCs will always be able to detect and defend against even complex and multi-stage attacks. In this way, SOC enables the proactive and preventive search for vulnerabilities across all IT and OT levels, while ensuring end-to-end response readiness in the event of actual attacks.
One thing is clear: If you want to securely leverage the benefits of IT/OT convergence and be ready for the networked industry of the future, you need to take a holistic view of cybersecurity. However, it is also clear that this requires internal resources and special skills that are often not available in times of a shortage of specialists.
Yokogawa Deutschland GmbH, Düsseldorf
IT/OT SOC: Advantages in detail
A key benefit of an IT/OT SOC is being able to detect threats automatically. This can help reduce the cost of manual reviews and increase employee productivity. A SOC can also help meet regulatory and industry requirements for IT security and protect data and systems from attacks and data loss.
Another benefit of an IT/OT SOC is the quality of the response. SOC has experienced IT security professionals who are knowledgeable about the latest threats and their protective measures. They can respond faster and more effectively to prevent attacks and minimize damage.
IT/OT-SOC enables automated monitoring and timely threat detection, reduces costs, increases employee productivity, and meets compliance.