Digitisation is sweeping through the various sectors of the economy and does not stop at the process industry. For example, field devices are being connected directly to the control system via appropriate interfaces and access is being created for mobile end devices so that all the possibilities of process monitoring can be fully exploited. If the aspect of cyber security is not taken into account, the increasing networking of systems can open up gateways for attackers. Vulnerabilities such as insecure or faulty device configurations, outdated software versions or unfavorable network infrastructures, for example, enable malware to be implemented, denial-of-service attacks to be carried out or sensitive data, such as recipes, to be stolen.
However, not only intentional attacks, but also negligent misconduct – for example during a service call – can lead to sabotage, resulting in component or system failures. Due to the critical processes within the process industry, this can result in considerable personal injury, environmental damage and damage to the company‘s image. And although more than half of industrial companies have already been victims of cyber attacks, there are still companies that are not aware of these risks and do not implement countermeasures.
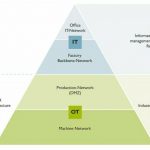
In order to protect supply chains from potential consequences nonetheless, critical infrastructure thresholds are constantly being developed and tightened. This puts the obligation on more and more companies to look at the risks of cyber attacks and integrate appropriate measures into their security management mechanisms. Companies are receiving support from various efforts. While the ISO 27000 series has established itself in the office or IT environment, the international IEC 62443 series of standards sheds light on OT areas, which comprise completely different systems and structures compared to IT environments.
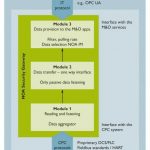
Against this background, Namur has, for example, developed the Namur Open Architecture (NOA) so that the data generated by smart field devices can be made more usable and plants can be operated more efficiently due to additional monitoring and optimisation functions. The concept described in NE 175 is implemented by adding a parallel NOA side channel to the automation pyramid. This picks up data from the field and sends it to the superordinate control level without retroactive effects, so that sensitive processes are not negatively influenced.
The NOA Security Gateway, which is to be installed between the process and monitoring areas, ensures that there is no retroactive effect. The gateway is defined in NE 177 by basic requirements based on the component and system requirements of IEC 62443. In addition, a zone model describes the mutual delimitation of the individual components of the gateway. On the one hand, the NOA Security Gateway consists of the Data Aggregator module, which establishes the coupling to the core process and is responsible for data acquisition. In addition, there is the module for one-way data transfer, which provides secure protection against backlash and decouples the data accordingly. The third module makes the data available for the monitoring area via OPC UA, for example. With a PLCnext controller and a Hart gateway, Phoenix Contact already offers a device combination with which the functions of the NOA Security Gateway can be implemented while largely meeting the requirements. The concept shows that future structures and systems can be designed securely, using IEC 62443, which was specially designed for automation areas and is constantly being further developed, as a basis. This approach is supported by secure components from Phoenix Contact, which are designed according to a certified development process in compliance with IEC 62443.
Holistic security concept
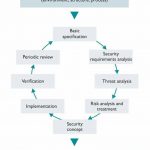
In order to support its customers in the design of a security concept based on IEC 62443 and the implementation of effective components, Phoenix Contact has been following a blueprint approach for several years. In this process, the specialists work out a holistic security concept with organisational and technical protective measures on the basis of a generic application in accordance with IEC 62443 – taking into account a prescribed cyclical process. The resulting solution ultimately contains measures to be implemented at the enterprise, solution, and component levels.
At the enterprise level, Phoenix Contact recommends, for example, restricting and monitoring access to solutions. In addition, components should be used for remote access that support VPN (Virtual Private Network), for example, and provide options for user authentication. One of the most important measures is to train and sensitise employees so that they live the measures developed and act accordingly.
At the solution level, the security experts advocate measures such as segmenting the solution into zones and protecting them with firewalls to prevent the spread of malware. Furthermore, activities within the solution should be monitored and any unusual occurrences should be responded to. This can be implemented through
proper logging or an anomaly detection system implemented in the solution.
For the component level, appropriate devices that support secure protocols and provide device hardening measures should generally be selected. In any case, default user names and passwords should be changed and unused services and interfaces should be disabled. Finally, the company‘s customers can refer to such recommendations and the associated detailed descriptions of measures.
The security specialists at Phoenix Contact are currently working on industry-specific security blueprints that users can use as templates for real systems. In this way, existing topologies with selected components, verified documents, and tools can be used, thus benefiting from the company‘s experience. Another advantage of security blueprints is that only deviations from the generic application or its security concept need to be re-examined in real systems. This makes it possible to develop security concepts much faster and more cost-effectively.
Phoenix Contact GmbH & Co. KG, Blomberg
Hall 11.1, Booth A27